- EC-Council
- Certified Ethical Hacker (CEH v.13 AI)
- Computer Hacking Forensic Investigator (C|HFI)
- Certified Penetration Testing Professional (CPENT)
- EC-Council Certified Incident Handler (ECIH)
- Certified SOC Analyst (CSA)
- Certified Chief Information Security Officer (CCISO)
- Certified Network Defender (C|ND)
- Certified Threat Intelligence Analyst (C|TIA)
- Certified Application Security Engineer (CASE) JAVA
- Certified Cloud Security Engineer (C|CSE)
- ISACA
- OFFENSIVE SECURITY
- CompTIA
- CISCO
- AWS
- Microsoft
- Mile2
- ORACLE
- INE/E-learn
- TCM Security
- Altered security
- PMI
- VMWARE
- CITRIX
- Linux Red hat
CYBERTECH INFOSOLUTIONS is a leading Ethical Hacking Training Institute in Mumbai
Categories
EC-Council, Certified Ethical Hacker (CEH v.13 AI)
Certified Ethical Hacker Certification - CEH v.13 AI
CEH v13 AI (Certified Ethical Hacker version 13) is the latest iteration of the Certified Ethical Hacker certification offered by EC-Council, with a focus on integrating artificial intelligence (AI) into the field of ethical hacking and cybersecurity.
- Contact us: +91 9372188252
- Email Id: contact@cybertechinfosolutions.com
- Course Level: Intermediate
- Course Delivery : Online / Offine
- Language: Hindi, English
- Accreditation by: EC-Council
What’s New in CEH v13 AI?
The C|EHv13 (Certified Ethical Hacker) Program is the top ethical hacking certification in the world and the accepted benchmark for cybersecurity professionals in more than 49 job roles worldwide.
In today’s highly competitive world, more than 93% of professionals pick C|EH for career advancement, and more than 50% of them are promoted after getting C|EH, according to recent research. Because of this, the C|EH certificate is in high demand, and we are excited to assist you in starting your path to being a proficient ethical hacker.
With the innovative Learn, Certify, Engage, and Compete Learning Framework included in the C|EHv13, you will gain the abilities and information required to become a skilled ethical hacker. In the field of cybersecurity, the Certified Ethical Hacker (CEH) certificate is widely accepted, and the most recent edition, CEH v13 AI, introduces significant ground-breaking innovations. With cyber risks evolving and cutting-edge technologies like artificial intelligence being integrated, CEH v13 emphasizes equipping professionals to handle modern problems.
This article will dive deep into what’s new in CEH v13, with a special concentration on AI, comparing it with v12, and providing an overview of the updated modules, hands-on labs, and exam structure.
Let's talk
5 Phases of the Ethical Hacking Framework Enhanced by AI
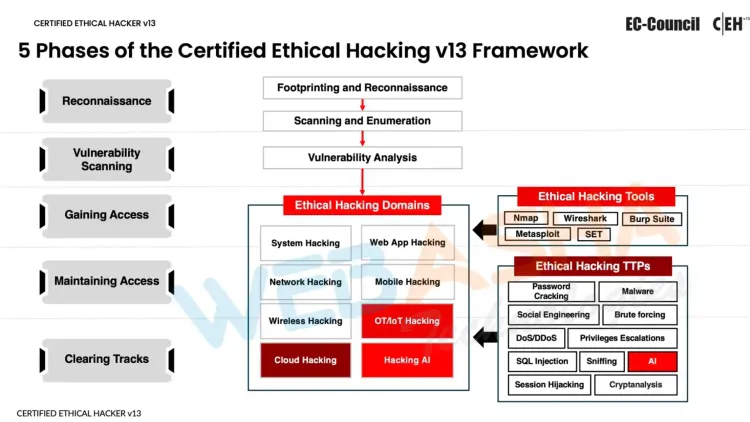
New Features and Modules in CEH v13 AI
A number of new courses are included in CEH v13 AI, many of which concentrate on integrating machine learning and artificial intelligence into cybersecurity procedures. This edition places a strong emphasis on practical application and firsthand knowledge. Here’s a deeper look at a few of the most significant updates:
AI and Machine Learning in Cybersecurity
A renewed emphasis on the offensive and defensive applications of AI in cyber operations.
Enhanced Hands-On Labs
With the use of AI-powered technologies, these hands-on exercises now enable learners to practice hacking in settings that mimic actual cyber threats.
Updated Threat Detection Methods
Using AI-driven analytics, CEH v13 teaches people how to identify dangers more effectively.
CEHv13 AI Exam Info
- Total Number of Modules: 20
- Total Number of Labs : 221 (91 Core Labs + 130 self study labs available on upgrade)
- Total Number of New Labs : 130
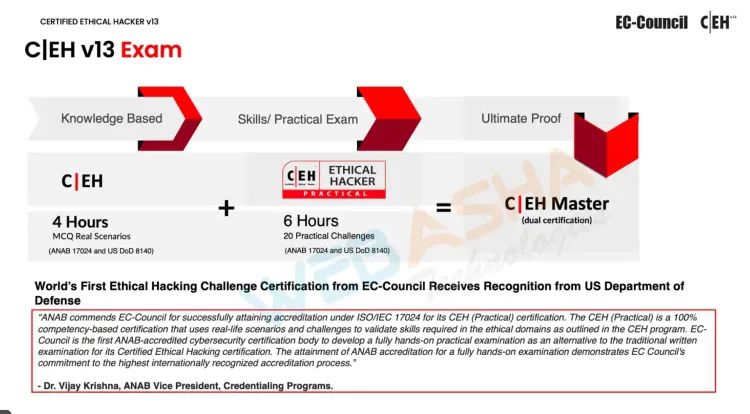
- Exam : 125 Questions (MCO)
- Exam Duration : 4 Hours
CEH V13 AI Certification Updates
CEHv13 AI Course Content
Cover the basics of key issues within the information security world, as well as the fundamentals of ethical hacking, data security controls, relevant laws, and standard procedures.
Learn how to use the newest techniques and tools to perform foot printing and reconnaissance, a important pre-attack part of the ethical hacking method.
Learn completely different network scanning techniques and countermeasures.
Learn various enumeration techniques, like Border gateway Protocol (BGP) and Network File Sharing (NFS) exploits, and associated countermeasures.
Learn how to spot security loopholes in a target organization’s network, communication infrastructure, and finish systems.
Learn about the various system hacking methodologies—including steganography, steganalysis attacks, and covering tracks—used to find system and network vulnerabilities.
Get an introduction to the various forms of malware, like Trojans, viruses, and worms, as well as system auditing for malware attacks, malware analysis, and countermeasures.
Learn about packet-sniffing techniques and the way to use them to find network vulnerabilities, as well as countermeasures to defend against sniffing attacks.
Learn social engineering concepts and techniques, as well as a way to determine theft makes an attempt, audit human-level vulnerabilities, and recommend social engineering countermeasures.
Learn about completely different Denial of Service (DoS) and Distributed DoS (DDoS) attack techniques, as well because the tools wont to audit a target and devise DoS and DDoS countermeasures and protections.
Understand the various session hijacking techniques wont to discover network-level session management, authentication, authorization, and cryptographic weaknesses and associated countermeasures.
Get introduced to firewall, intrusion detection system, and honeypot evasion techniques; the tools wont to audit a network perimeter for weaknesses; and countermeasures.
Learn about web server attacks, as well as a comprehensive attack methodology wont to audit vulnerabilities in web server infrastructures and countermeasures.
Learn about web application attacks, as well as a comprehensive web application hacking methodology wont to audit vulnerabilities in web applications and countermeasures.
Learn about SQL injection attack techniques, injection detection tools, and countermeasures to find and defend against SQL injection makes an attempt.
Learn about wireless encryption, wireless hacking methodologies and tools, and Wi-Fi security tools.
Learn about mobile platform attack vectors, android vulnerability exploits, and mobile security pointers and tools.
Learn how to secure and defend net of Things (IoT) and operational technology (OT) devices and possible threats to IoT and OT platforms.
Learn completely different cloud computing ideas, like container technologies and server less computing, numerous cloud-based threats and attacks, and cloud security techniques and tools.
In the final module, study cryptography and ciphers, public-key infrastructure, cryptography attacks, and cryptanalysis tools.
